Fluxion – WPA/WPA2 Security Hacked Without Brute Force
Fluxion is a remake of linset by vk496 with less bugs and more features. It’s compatible with the latest release of Kali (Rolling). Latest builds (stable) and (beta) HERE . If you new, please start reading the wiki
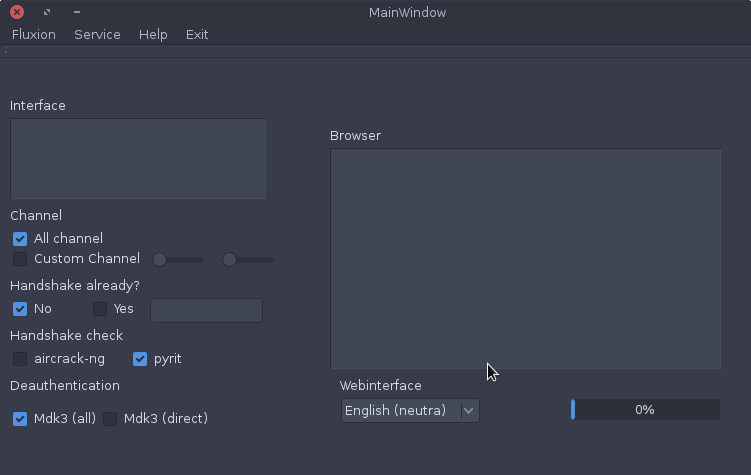
How it works:
Step 1: Scan the networks.
Step 2: Capture a handshake (can’t be used without a valid handshake, it’s necessary to verify the password)
Step 3: Use WEB Interface *
Step 4: Launch a FakeAP instance to imitate the original access point
Step 5: Spawns a MDK3 process, which deauthenticates all users connected to the target network, so they can be lured to connect to the FakeAP and enter the WPA password.
Step 6: A fake DNS server is launched in order to capture all DNS requests and redirect them to the host running the script
Step 7: A captive portal is launched in order to serve a page, which prompts the user to enter their WPA password
Step 8: Each submitted password is verified by the handshake captured earlier
Step 9: The attack will automatically terminate, as soon as a correct password is submitted
Step 2: Capture a handshake (can’t be used without a valid handshake, it’s necessary to verify the password)
Step 3: Use WEB Interface *
Step 4: Launch a FakeAP instance to imitate the original access point
Step 5: Spawns a MDK3 process, which deauthenticates all users connected to the target network, so they can be lured to connect to the FakeAP and enter the WPA password.
Step 6: A fake DNS server is launched in order to capture all DNS requests and redirect them to the host running the script
Step 7: A captive portal is launched in order to serve a page, which prompts the user to enter their WPA password
Step 8: Each submitted password is verified by the handshake captured earlier
Step 9: The attack will automatically terminate, as soon as a correct password is submitted
Requirements:
- Linux operating system
- Kali Linux 2 or Kali 2016.1 rolling
- Kali 2 & 2016 support the latest aircrack-ng versions
- External Wi-Fi card is recommended
DISCLAIMER: In our tutorials we only EVER hack our own systems as a proof of concept and never engage in any black hat activity.





0 comments: