Smart Pentester is an SSH based Penetration Testing Framework. It provides a GUI for well known tools like nmap, hping, tcpdump, volatili...
Sunday, May 31, 2015Tribler is a research project of Delft University of Technology. Tribler was created over nine years ago as a new open source Peer-to-Pee...
Sunday, May 31, 2015Tribler - Download Torrents using Tor-inspired onion routing
Sunday, May 31, 2015 Sensei Fedon 0 Comments
Exploit Pack, is an open source GPLv3 security tool, this means it is fully free and you can use it without any kind of restriction. Othe...
Sunday, May 31, 2015Exploit Pack - Open Source Security Project for Penetration Testing and Exploit Development
Sunday, May 31, 2015 Sensei Fedon 0 Comments
SNMP brute force, enumeration, CISCO config downloader and password cracking script. Listens for any responses to the brute force community...
Sunday, May 31, 2015SNMP Brute - Fast SNMP brute force, enumeration, CISCO config downloader and password cracking script
Sunday, May 31, 2015 Sensei Fedon 0 Comments
- metasploit
- snmpwalk
- snmpstat
- john the ripper
PackETH is GUI and CLI packet generator tool for ethernet. It allows you to create and send any possible packet or sequence of packets on ...
Saturday, May 30, 2015PackETH - Ethernet Packet Generator
Saturday, May 30, 2015 Sensei Fedon 0 Comments
PackETH is GUI and CLI packet generator tool for ethernet. It allows you to create and send any possible packet or sequence of packets on the ethernet link. It is very simple to use, powerful and supports many adjustments of parameters while sending sequence of packets. And lastly, it has the most beautiful web site of all the packet generators.
CMSmap is a python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs. The main purpo...
Saturday, May 30, 2015CMSmap - Scanner to detect security flaws of the most popular CMSs (WordPress, Joomla and Drupal)
Saturday, May 30, 2015 Sensei Fedon 0 Comments
CMSmap is a python open source CMS scanner that automates the process of detecting security flaws of the most popular CMSs. The main purpose of CMSmap is to integrate common vulnerabilities for different types of CMSs in a single tool.
Continuously jam all wifi clients and access points within range. The effectiveness of this script is constrained by your wireless card. ...
Saturday, May 30, 2015WiFiJammer - Continuously Jam All WiFi Clients/Routers
Saturday, May 30, 2015 Sensei Fedon 0 Comments
Saturday, May 30, 2015
Saturday, May 30, 2015
Saturday, May 30, 2015
Saturday, May 30, 2015
There are some simple keyboard shortcuts which one can use while using Internet and it would help the user to avoid typing a lot and also a...
Saturday, May 30, 2015Top Ten Simple and Useful Internet Tricks That You May Not Know
Saturday, May 30, 2015 Sensei Fedon 0 Comments
Saturday, May 30, 2015
Packet Sender is an open source utility to allow sending and receiving TCP and UDP packets. It is available free (no ads / no bundlewar...
Saturday, May 30, 2015Packet Sender The Free Network Test Utility
Saturday, May 30, 2015 Sensei Fedon 0 Comments
 utility to allow sending and receiving TCP and UDP packets. It is available free (no ads / no bundleware) for Windows, Mac, and Linux. It can be used for both commercial and personal use (license). It's designed to be very easy to use while still providing enough features for power users to do what they need.
utility to allow sending and receiving TCP and UDP packets. It is available free (no ads / no bundleware) for Windows, Mac, and Linux. It can be used for both commercial and personal use (license). It's designed to be very easy to use while still providing enough features for power users to do what they need.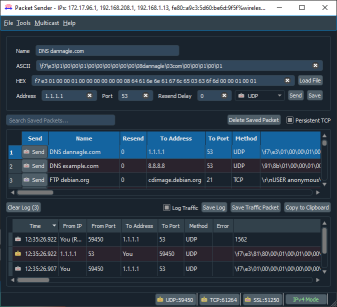 Windows Screenshot | 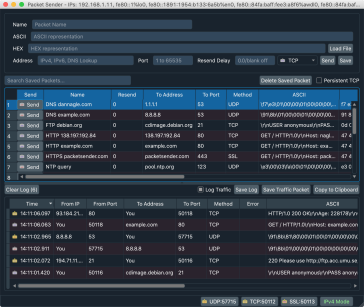 Mac Screenshot |
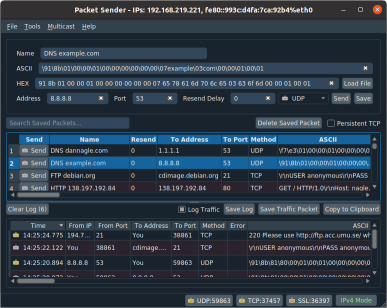 Ubuntu Screenshot | 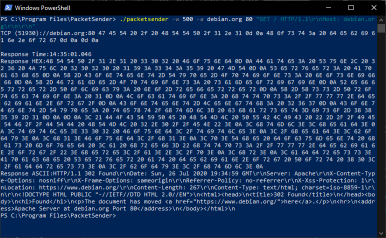 Command Line Screenshot (Comes with all desktop versions) |
When scraping the Google search engine, we need to be careful so that Google doesn’t detect our automated tool as a bot, which will redirec...
Monday, May 25, 2015Google Hacking with GGGoogleScan
Monday, May 25, 2015 Sensei Fedon 0 Comments
Friday, May 15, 2015
New Tool: The PenTesters Framework (PTF) Released
Friday, May 15, 2015 Sensei Fedon 0 Comments
The Washington Post site temporarily shut down after being hacked by Syrian Electronic Army (SEA) One of the most successful hacking ...
Friday, May 15, 2015Syrian Electronic Army Hacks the Washington Post and redirects users to SEA’s website
Friday, May 15, 2015 Sensei Fedon 0 Comments
The Washington Post site temporarily shut down after being hacked by Syrian Electronic Army (SEA)
Background The PoC for SockStress, written in C, has NEVER worked for me (that’s not to say it doesn’t work…that’s just to say I suck a...
Wednesday, May 13, 2015SOCKSTRESS DENIAL OF SERVICE WITH PYTHON
Wednesday, May 13, 2015 Sensei Fedon 0 Comments
Background
An Apache HTTP server in production environments can be under attack in various different ways. Attackers may attempt to gain access to una...
Monday, May 11, 2015How to configure fail2ban to protect Apache HTTP server
Monday, May 11, 2015 Sensei Fedon 0 Comments
Are you tired of getting multi-thousand line emails from the logcheck package that contain multiple reports of denied queries from named? I...
Monday, May 11, 2015Blocking a DNS DDOS using the fail2ban package
Monday, May 11, 2015 Sensei Fedon 0 Comments
Recently one of our client server was subjected to DDOS attack. We use Nginx’s Limit Req Module and fail2ban together to thwart this at...
Monday, May 11, 2015Survive DDOS attack with Nginx's and fail2ban
Monday, May 11, 2015 Sensei Fedon 0 Comments
Installing fail2ban
apt-get install fail2banConfiguration
Basic installation and configuration of fail2ban on CentOS 7 (RHEL7) for ssh access. (Changing some of the default values) Add EPEL repos...
Monday, May 11, 2015fail2ban on CentOS 7 for ssh access
Monday, May 11, 2015 Sensei Fedon 0 Comments
(Changing some of the default values)
- Add EPEL repositories
wget http://epel.mirror.nucleus.be/7/x86_64/e/epel-release-7-1.noarch.rpm rpm -i epel-release-7-1.noarch.rpm
- Install packages
yum install fail2ban-firewalld fail2ban-systemd
- create /etc/fail2ban/jail.local
[DEFAULT] findtime = 5000 [sshd] enabled = true
- Create /etc/fail2ban/action.d/firewallcmd-ipset.local
[Init] bantime = 10000
- Enable and start fail2ban:
systemctl enable fail2ban systemctl start fail2ban
- Check if selinux isn't blocking fail2ban from accessing the logs
tail /var/log/audit/audit.log
DARPA’s Memex search engine touted to be a Google-killer When we look at the history of computing, it features a string of organization...
Thursday, May 07, 2015Is DARPA’s new search engine, Memex a Google-killer?
Thursday, May 07, 2015 Sensei Fedon 0 Comments
DARPA’s Memex search engine touted to be a Google-killer
Automated incident response for the rest of us Netflix has released source code for its automated incident response tool to help organi...
Thursday, May 07, 2015Netflix looses FIDO hack attack dog as open source
Thursday, May 07, 2015 Sensei Fedon 0 Comments
Automated incident response for the rest of us

(D)DoS Deflate is a lightweight bash shell script designed to assist in the process of blocking a denial of service attack. It utilizes th...
Wednesday, May 06, 2015Installing (D)DoS Deflate To Mitigate DDoS Attack
Wednesday, May 06, 2015 Sensei Fedon 0 Comments
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nLynis is a security auditing tool for Unix and Linux based systems. It performs in-depth security scans, with almost no configuration, T...
Wednesday, May 06, 2015Lynis – Security Auditing Tool for Unix/Linux
Wednesday, May 06, 2015 Sensei Fedon 0 Comments
- AIX
- FreeBSD
- HP-UX
- Linux
- Mac OS
- NetBSD
- OpenBSD
- Solaris
A recent Department of Homeland Inspector General report focused mostly on U.S. Coast Guard insider threats, stating, “Trusted insiders c...
Wednesday, May 06, 2015Maritime Cybersecurity Firm: 37% of Microsoft Servers On Ships Vulnerable To Hacking
Wednesday, May 06, 2015 Sensei Fedon 0 Comments
We will show you how to program your drone so it takes off, moves around and does a flip. First of you will need to download and install...
Wednesday, May 06, 2015How to program your drone
Wednesday, May 06, 2015 Sensei Fedon 0 Comments
var arDrone = require('ar-drone'); var client = arDrone.createClient(); client.takeoff(); client .after(5000, function() { this.clockwise(0.5); }) .after(3000, function() { this.animate('flipLeft', 15); }) .after(1000, function() { this.stop(); this.land(); });
So you are in college or in a firm where you operate behind a proxy server. The company and colleges have placed many restrictions on many ...
Wednesday, May 06, 2015How to Download Torrents Online Using IDM? 4 Working Ways for You!
Wednesday, May 06, 2015 Sensei Fedon 0 Comments
About
Network security blog.
Follow Us
Popular Posts
-
Eternalromance is another SMBv1 exploit from the leaked NSA exploit collection and targets Windows XP/Vista/7 and Windows Server 2003 and 2...
-
context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
-
A web application firewall (WAF) is an appliance, server plugin, or a software filter that applies a set of rules to an HTTP conversatio...
-
I was just checking out my posts on Techotoys and found that I haven't posted any tutorial on how to hack Website. There are many tool...
-
Learn how to hack Wi-Fi password of modern routers Wifi password hacking has become popular as people are always in search of the free i...
-
LazyKali is an awesome script written in bash shell. It can automate the whole update and install new tools in your hack repository. As the...
-
XSS Rays is a complete XSS reversing/scanner tool. It helps you to find how a site is filtering code, and allows you to check for injecti...
-
BruteSploit is a collection of method for automated Generate, Bruteforce and Manipulation wordlist with interactive shell. That can be use...
Labels
Total Pageviews
Blog Archive
-
▼
2015
(57)
-
▼
May
(31)
- Webfwlog - Firewall Log Analyzer
- Smart Pentester - An SSH based Penetration Testing...
- Tribler - Download Torrents using Tor-inspired oni...
- Exploit Pack - Open Source Security Project for Pe...
- SNMP Brute - Fast SNMP brute force, enumeration, C...
- PackETH - Ethernet Packet Generator
- CMSmap - Scanner to detect security flaws of the m...
- WiFiJammer - Continuously Jam All WiFi Clients/Rou...
- netool.sh - MitM Pentesting Opensource T00lkit
- MobaXterm - Terminal for Windows with X11 server, ...
- Bacula - Network Backup Tool for Linux, Unix, Mac,...
- SmarTTY - Multi-tabbed SSH Client with SCP Support
- Top Ten Simple and Useful Internet Tricks That You...
- INURLBR - Advanced Search in Multiple Search Engines
- Packet Sender The Free Network Test Utility
- Google Hacking with GGGoogleScan
- New Tool: The PenTesters Framework (PTF) Released
- Syrian Electronic Army Hacks the Washington Post a...
- SOCKSTRESS DENIAL OF SERVICE WITH PYTHON
- How to configure fail2ban to protect Apache HTTP s...
- Blocking a DNS DDOS using the fail2ban package
- Survive DDOS attack with Nginx's and fail2ban
- fail2ban on CentOS 7 for ssh access
- Is DARPA’s new search engine, Memex a Google-killer?
- Netflix looses FIDO hack attack dog as open source
- Installing (D)DoS Deflate To Mitigate DDoS Attack
- Lynis – Security Auditing Tool for Unix/Linux
- Maritime Cybersecurity Firm: 37% of Microsoft Serv...
- How to program your drone
- How to Download Torrents Online Using IDM? 4 Worki...
- WTO Hacked
-
▼
May
(31)
Popular Posts
-
This article aims to introduce the framework that has been disclosed through an article posted by ShadowBrokers , focusing on two...
-
A web application firewall (WAF) is an appliance, server plugin, or a software filter that applies a set of rules to an HTTP conversatio...
-
Elite Proxy Switcher The Best Tool That I Ever Find on The Internet For Finding And Checking Huge Proxy Lists You Can Find Elite and A...
-
context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
-
Hi guys, today i am goint to tell you a perfect program which makes Effective DoS Attacks Easly :D Name of the Program is DoS-Pro v 2.0 R...
-
It is time to make some attacks which like ddos but from only one PC :D DecFlooder-v1.00 Hack Tools easy to use as you see from the p...
-
Below are the inside details of Florida voting systems. If the United States government can't even keep their ballot systems secure, why...


















0 comments: